Ryuk is developed with a great deal of targeted Ransomeware, which is run by the prime sophisticated group “GRIM SPIDER.” The target was started in August 2018 to get the high ransom from the high revenue-generating business organization. This system also called “Big Game Hunting,” where the changes in action for WIZARD SPIDER. This Russian based criminal enterprise threat group primarily focused on financial fraud by using IT or telecommunication, which is called “TrickBot banking malware.”
If you are familiar with the Hermes, Bitpaymer, and Samas, then Ryuk is very much similar to this malware, which mostly targets the environments of the enterprise. While searching for Ryuk ransomware virus information, another thing has been revealed that the versions code of Ryuk is similar to Hermes ransomware. It is confirmed that Ryuk is derived from Hermes source code and the development is balanced from the begging. But the function of Ryuk is very much different from Hermes ransomware, where GRIM SPIDER uses ryuk to target the environment of big business.
Ransom Note By Ryuk:
When every Ryuk ransomware plays Big Game Hunting and attacks any high organization, then Ryuk left a sweet ransom note “RyukReadMe.txt.” where important details are mention for the organization. In most cases, there are two types of Ransom note “Pleasant long note” & “Shorter less detail note.”
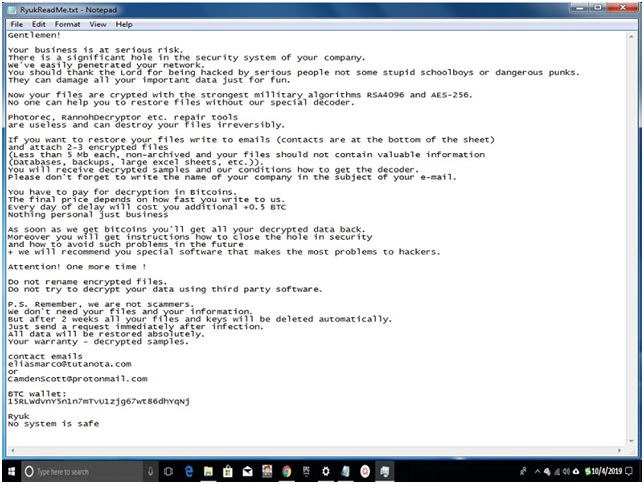
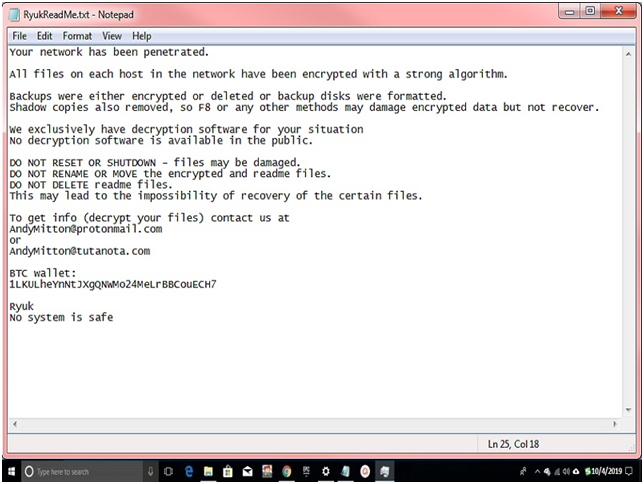
According to the record found on the internet about Ryuk ransomware that across 52 transactions, it has acquired 705.80 BTC and the current value of US$3,701,893.98 in total.
Important Function of Ryuk Ransomware
- Ryuk didn’t even bother to adjust the marker as the code used to create in the encrypted files.
- The feature invokes the above-mentioned routine in Ryuk.
- In the same direction, the batch script called “window.bat” is used to delete volumes of shadows and backup data.
- Files are dropped to the disk that looks like in name and purpose.
- Ryuk’s entire logic is retained in both the 32 and 64-bit versions
- Code across multiple architectures could well be a representation of an identical source code underlying it.
- Ryuk’s dropper is straightforward and simple.
- Using the srand function and GetTickCount for seed generation, the dropper generates a 5-lettered random file name at the start of Ryuk execution.
- Depending on the version of Windows on the victim’s computer, the aforementioned payload files are then written to a folder.
- If the development of the file fails, the dropper tries to write it in its own directory, using its own name and the last character being the letter ‘V.’
- The dropper then checks if the system is running under Wow64 after generating the file and writes the correct payload based on the outcome of the search.
- Ryuk uses a rather simple injection technique whereby they first use OpenProcess to get a handle on the target process and use VirtualAllocEx to assign a buffer in their address space.
- The code inserted includes the core functionality used by the file encryption ransomware.
- Ryuk inserts software began by decrypting a list of the names “API” function strings. I am using a predefined key and a string length range that is then used to load the corresponding functions dynamically.
Final Words:
Ryuk ransomware is a big game hunter formally support by GRIM SPIDER. Many companies get busted by Ryuk malware and in against paid huge bucket of ransom. Using active malware, Antivirus can stop the hackers from digging into your PC. If you know, any new update related to Ryuk and wants to share with us, then use the comment box. Also, don’t forget to share this Ryuk information with your family and friends.






![SIMS 4 Download Free For PC Full Version 2019 [UPDATED] SIMS 4 Download](https://www.geniustechie.com/wp-content/uploads/2019/03/SIMS-4-Download-100x70.jpg)


